I have received similar questions from several people who wrote to me to my personal mail. Initially, I try to reply to the sender directly, but i think it is better to build a list here in the blog so that the other people can join in to discuss and record our history. Below are my own thinking and if you have better answer, I sincerely request you to feedback to us.
Q1. Write a protocol, based on Needham-Schroeder, to establish a shared key between three parties, Alice, Bob and Carol using a KDC. Each party trusts the KDC and, at the end of the protocol, should have a common key and be confident that the other two parties also have it.
Ans: Needham-Schroeder Protocol is the basis form of Kerberos protocol. In this protocol, there is a trusted server by all the users known as KDC (Key Distribution Center). When the user want to communicate to other users, the user will request to KDC to generate a shared session key which the user and his intended counterpart can decrypt. It is the authentication between 2 parties. For 3 parties (A,B,C), the keys required will be more than one key with KeyAB, KeyAC and KeyBC (3 keys).
In case, you would like to have just one common key between 3 parties, then the protocol will be a little different. Basically, you will start with the keys shared between KDC and Alice, between KDC and Bob as well as between KDC and Carol. The trick to have the common key and to be confident that the other two parties also have it is to explicitly state the identities of other two parties.
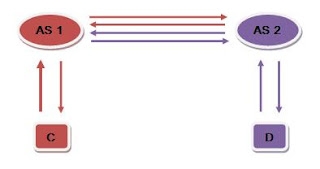
Q2. Write a symmetric{key inter{domain end{to{end authentication protocol. The environment includes two mobile service domains, each with an authentication server. We use AS1 and AS2 to denote the domains and the associated authentication servers. We restrict our attention to two users, Carol and Doug. Carol is registered with AS1 while Doug is registered with AS2. You are to design a protocol for the case where Carol has moved to AS2 and Doug has moved to AS1.
Registration in this symmetric key domain means the two parties have established a shared key which can be used as a basis for authentication. The two authentication servers, AS1 and AS2, share a symmetric key.
In this protocol, we have to assume that AS1 & C are in different inter-domain from AS2 & D. AS1 and AS2 are communicating with shared key between them. In order to register C to AS2, we will have the following steps.
1. C has to request to AS1 that he wanted to communicated with AS2.
2. AS1 will inform AS2 about C's request.
3. AS2 will reply to AS1 with the Key between C and AS2.
4. AS1 will send the key to C and AS2.
Now, there is key shared between C and AS2. Similarly, for D to register with AS1, it will follow the same steps. If you like to provide data freshness, you will need to add the nonces. If you want to provide integrity, you need to hash the key. For confidentiality, you got to ensure that key can be only decrypted by sender and intended receiver. For anonymity, you might want to consider the subliminal identity or nickname for C and D.
Q1. Write a protocol, based on Needham-Schroeder, to establish a shared key between three parties, Alice, Bob and Carol using a KDC. Each party trusts the KDC and, at the end of the protocol, should have a common key and be confident that the other two parties also have it.
Ans: Needham-Schroeder Protocol is the basis form of Kerberos protocol. In this protocol, there is a trusted server by all the users known as KDC (Key Distribution Center). When the user want to communicate to other users, the user will request to KDC to generate a shared session key which the user and his intended counterpart can decrypt. It is the authentication between 2 parties. For 3 parties (A,B,C), the keys required will be more than one key with KeyAB, KeyAC and KeyBC (3 keys).
In case, you would like to have just one common key between 3 parties, then the protocol will be a little different. Basically, you will start with the keys shared between KDC and Alice, between KDC and Bob as well as between KDC and Carol. The trick to have the common key and to be confident that the other two parties also have it is to explicitly state the identities of other two parties.
Q2. Write a symmetric{key inter{domain end{to{end authentication protocol. The environment includes two mobile service domains, each with an authentication server. We use AS1 and AS2 to denote the domains and the associated authentication servers. We restrict our attention to two users, Carol and Doug. Carol is registered with AS1 while Doug is registered with AS2. You are to design a protocol for the case where Carol has moved to AS2 and Doug has moved to AS1.
Registration in this symmetric key domain means the two parties have established a shared key which can be used as a basis for authentication. The two authentication servers, AS1 and AS2, share a symmetric key.
In this protocol, we have to assume that AS1 & C are in different inter-domain from AS2 & D. AS1 and AS2 are communicating with shared key between them. In order to register C to AS2, we will have the following steps.
1. C has to request to AS1 that he wanted to communicated with AS2.
2. AS1 will inform AS2 about C's request.
3. AS2 will reply to AS1 with the Key between C and AS2.
4. AS1 will send the key to C and AS2.
Now, there is key shared between C and AS2. Similarly, for D to register with AS1, it will follow the same steps. If you like to provide data freshness, you will need to add the nonces. If you want to provide integrity, you need to hash the key. For confidentiality, you got to ensure that key can be only decrypted by sender and intended receiver. For anonymity, you might want to consider the subliminal identity or nickname for C and D.
Hi,
ReplyDeleteI'm going to take CSCI361 & CSCI368 next sem, so would like to know for the topics that are going to be covered for 368 like the different protocols etc that will be taught so that i could do some early reading. would appreciate much the tips & input. If anyone has any tips or reading to be done for 361, the help would be greatly appreciated as well. Thanks